
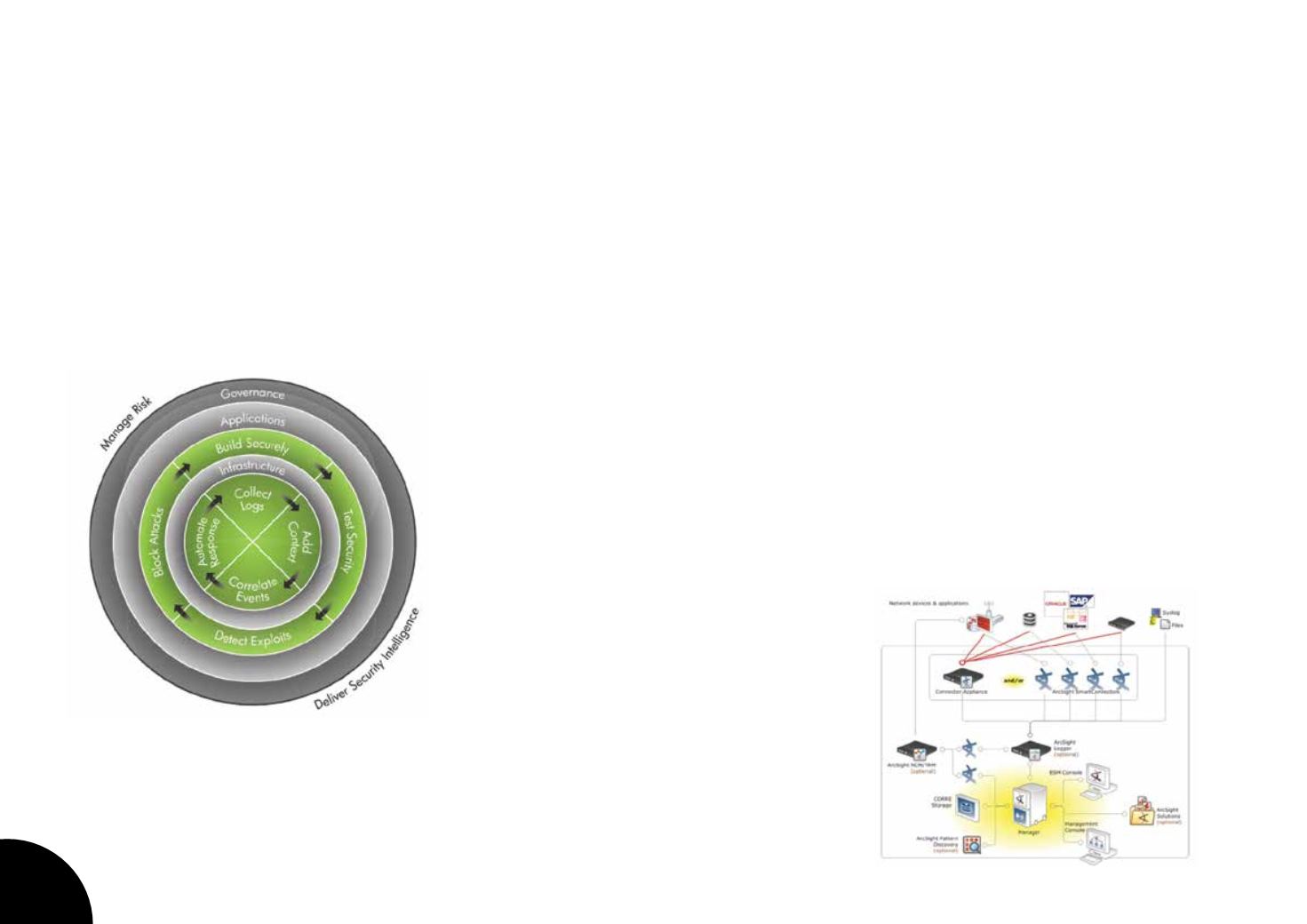
Data aggregation:
Log management aggregates
data from many sources, including network, security,
servers, databases, applications, providing the ability to
consolidate monitored data to help avoid missing crucial
events.
Compliance:
Applications can be employed to automate
the gathering of compliance data, producing reports
that adapt to existing security, governance and auditing
processes.
Retention:
employing long-term storage of historical
data to facilitate correlation of data over time, and
to provide the retention necessary for compliance
requirements. Long term log data retention is critical
in forensic investigations as it is unlikely that discovery
of a network breach will be at the time of the breach
occurring.
Forensic analysis:
The ability to search across logs on
different nodes and time periods based on specific
criteria. This mitigates having to aggregate log
information in your head or having to search through
thousands and thousands of logs.
Correlation:
looks for common attributes, and links
events together into meaningful bundles. This
technology provides the ability to perform a variety of
correlation techniques to integrate different sources, in
order to turn data into useful information. For example,
to track an AD user use of wireless network
Alerting:
the automated analysis of correlated events
and production of alerts, to notify recipients of
immediate issues. Alerting can be to a dashboard, or
sent via third party channels such as email.
Dashboards:
Tools can take event data and turn it into
informational charts to assist in seeing patterns, or
identifying activity that is not forming a standard
pattern.
A Security Information and Event Management or SIEM solution is a system that combines Security Incident
Management with Security Event Management. It is used to provide real time analysis of the security alerts that are
generated by various IT infrastructure components such as wired/wireless network devices, servers, firewall, etc.
For ISO27000 compliance and federal UAE regulations, UAE University has implemented a SIEM solution to log security
events and generate reports. The SIEM is based on the well known SIEM product called HP Arcsight. This product
has more advanced features than the typical SIEM solution and it is referred to as a Security Intelligence and Risk
Management SIRM Solution. It is capable of helps safeguard the organization by providing complete visibility into
activity across the IT infrastructure including external threats such as malware and hackers, internal threats such as
data breaches and fraud.
The system capabilities can are summarized
below
Security Information and Event Management SIEM Solution
60














